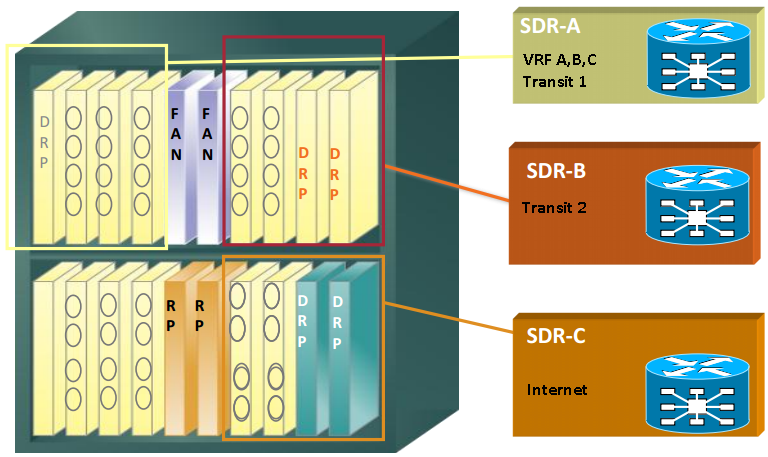
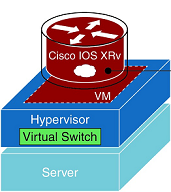
IOS-XR Secure Domain Router (SDR)
Before we start with SDR concept, we need an introduction about virtualization techniques for creating virtualized router entities. A Hardware-Isolated Virtual Router (HVR) has hardware-based resource isolation between routing entities, whereas a Software-Isolated Virtual Router (SVR) comprises software-based resource isolation between routing entities. Within SVRs, there are several models for achieving virtualization. One model allows … Read more